CSV Compare
Compare two CSV files and find differences with row matching and column selection.
- Match by row number or key column
- Select specific columns to compare
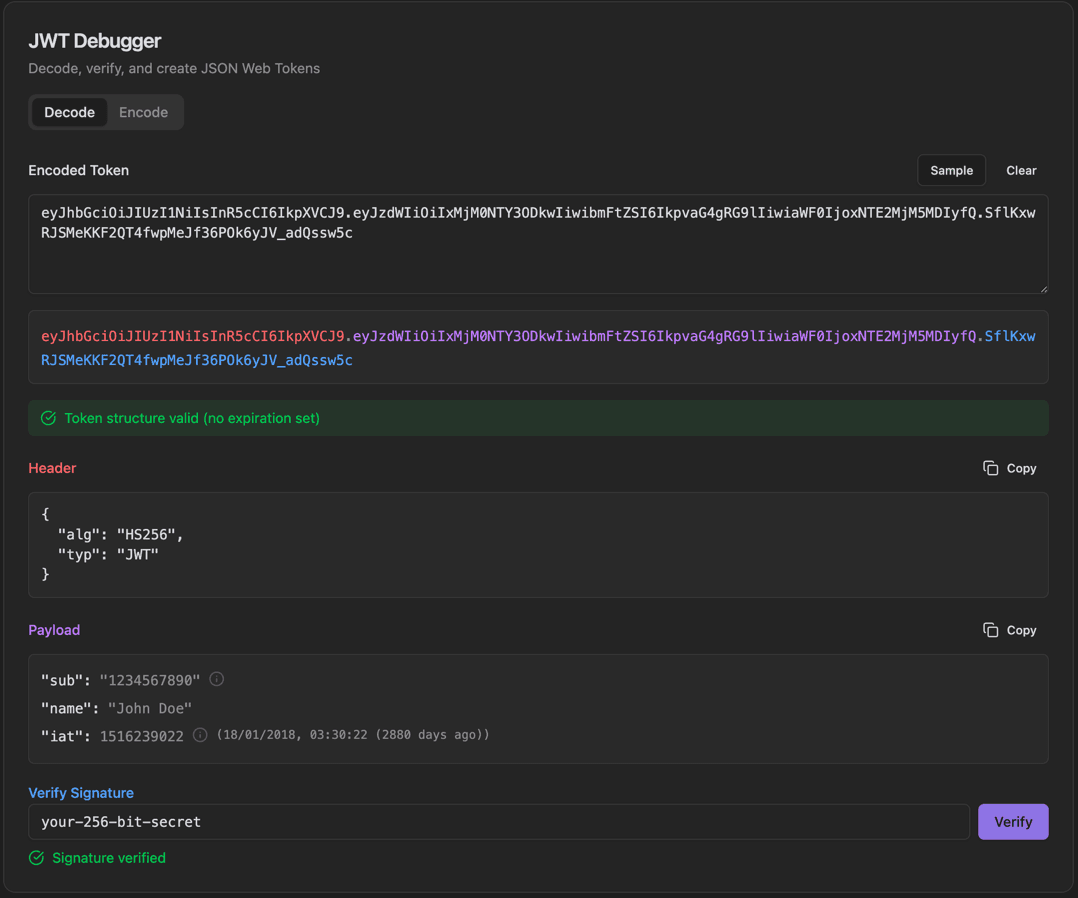
JSON Web Tokens (JWT) are the standard for secure information exchange in modern web applications. This debugger decodes tokens to show header and payload, verifies signatures with a secret key, and displays token validity status with human-readable timestamps.
Paste a JWT token in the Encoded Token field or click Sample
The token is automatically decoded and color-coded
View Header and Payload sections with Copy buttons
Enter the secret in Verify Signature and click Verify
Switch to Encode tab to create new tokens
Download PrimeUtils and get access to JWT Debugger plus 20+ other developer tools.